AI-Driven Autonomous SecOps
A hyperautomated platform unifying Ingestion, Detection and Response, powered by Forensic Analysis & Investigation
Scroll Down To Explore
Your Cybersecurity Journey
Swipe Down To Explore Your Cybersecurity Journey
Hyperautomated Autonomous Investigation with Human-in-the-Loop
Security teams are drowning in alerts, false positives, and manual investigations. Imperum changes the game with Hyperautomated Autonomous Investigation, powered by Local AI, ensuring seamless efficiency with human expertise when needed.
Fetches and processes data across your security ecosystem, vendor-agnostic and protocol-flexible.
Connects any technology, even legacy systems, via SSH, webhook, mail, Telnet, and more.
Executes response actions autonomously or escalates mission-critical cases.
Imperum Mobile App enables analysts to validate findings and take action in real-time.
Automatically generates detailed summaries and full investigation reports.
x5 times more affordable investment
than the traditional solutions on the market
Market’s Only Connector-Agnostic Platform
Seamlessly integrate new technologies without writing a single line of code.
Seamless Integration Beyond REST APIs
Integrate with protocols like Telnet, SSH, RDP, Webhooks, and CLI—no coding needed
600+ Collectors for Unmatched Forensics & Response
Combine the comprehensive visibility of EDR with the robust response capabilities of DFIR-Forensics.
Connect Directly with Processes, Not Just REST APIs
Whisper directly to the constraints of REST-API connections.
Deploy Your Way: On-Premise or Cloud
Seamless integration with native deployment options tailored to your needs.
MTTD
With our AI-powered advanced threat detection, reduce your Mean Time to Detect (MTTD) from weeks to hours, enabling faster and more efficient threat detection
MTTR
With our hyperautomation module, slash your Mean Time to Response (MTTR) from hours to minutes, ensuring rapid threat containment and remediation.
MTTI
With our AI-powered App Connector Wizard, reduce your Mean Time to Integrate (MTTI) from weeks to just three clicks for seamless and rapid deployment.
Your SecOps Journey without Imperum SecOps Platform
The cybersecurity talent shortage, combined with the increasing complexity of various GUIs and the lack of effective orchestration, is likely overwhelming your SecOps team — leading to burnout and missed critical alerts.
Multiple interfaces, complex front ends, and disconnected technologies are adding to your challenges, increasing complexity, inflating costs and driving up operational expenses.
Do These Sound Familiar to Your Security Team?
Delayed responses, manual data handling, and an overwhelming workload can make it difficult for your team to keep up.
The constant flood of security alerts leads to alert fatigue—where analysts become desensitized due to excessive notifications, increasing the risk of missed threats, slower response times, and burnout. As alerts pile up, distinguishing real threats from false positives becomes a daunting task, further straining your security team.
These challenges not only add unnecessary pressure but also reduce overall performance, efficiency, and the ability to respond to critical incidents in a timely manner
Unifying Security with Seamless Integration Across Multiple Diverse Technologies
Stuck with Fragmented Ingestion & SIEM Dependency?
Without an effective ingestion process, managing events, alerts, IOAs, and IOCs across diverse technologies like REST, GraphQL, WebHook, WebSocket, SOAP, and SYSLOG becomes fragmented and overly complex.
It often demands custom parsers, data normalization, and heavy reliance on SIEM systems to correlate information.
Seamless Ingestion for Complete Security Visibility
Imperum’s Ingest module seamlessly collects events, alerts, IOAs, and IOCs from a wide range of security technologies—NGFW, DLP, SIEM, DDoS, ITSM, CTI, and more—using multiple protocols like Syslog, REST, GraphQL, Webhooks, RPC/gRPC, Websockets, and SOAP.
It normalizes raw data into structured event data, applying correlation, enrichment, and noise reduction to eliminate false positives and enhance security insights. With Imperum, you get clean, enriched, and actionable data for faster detection and response—all in real time.
How does this work?
a playbook
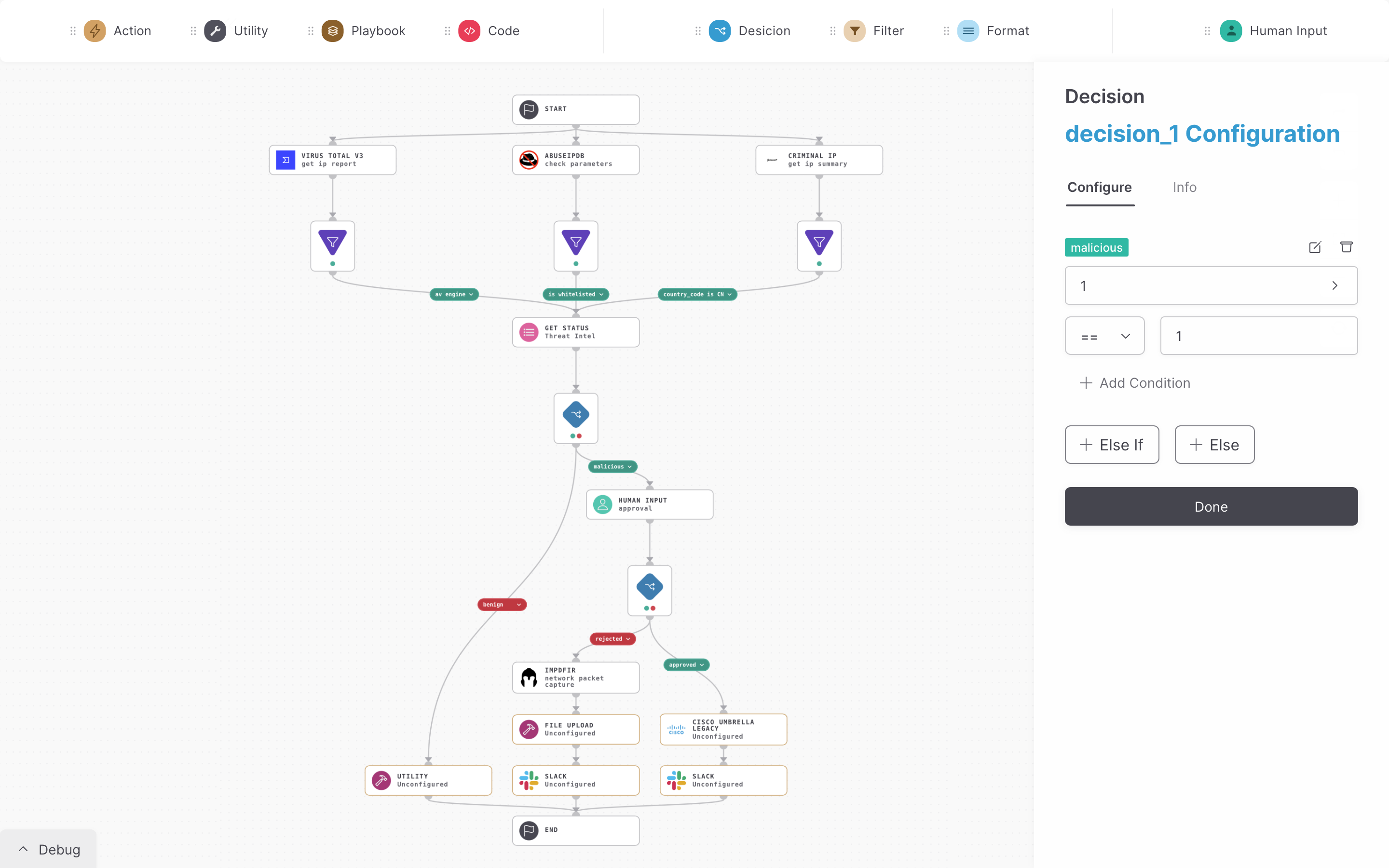
Our intuitive drag-and-drop interface allows you to effortlessly design and deploy unlimited playbook runs—no coding skills required. Simplify even the most complex workflows and maintain full control over your operations with a user-friendly system designed for maximum efficiency.
With Hyperautomate, you gain the power of No-Code SOAR combined with the versatility of Low-Code customization
How does this work?
Onboarding new technology with traditional SOAR solutions can take up to 5 to 6 months, with costs quickly escalating and draining your resources while you wait. This often means relying on professional services to fully leverage the SOAR capabilities you’ve already invested in — requiring additional investment just to access those capabilities.
While other companies may offer some connectors, if the connector you need isn’t available, they are unable to create one.
As a result, connecting your technology can lead to significant delays, consuming a massive amount of time.
This was one of the reasons why Gartner declared SOARs obsolete.
Our Hyperautomation is the only connector-agnostic SOAR in the market, allowing you to create custom REST-API connectors without any coding.
We’ve solved the connector challenge with an AI-powered parser and coding platform, eliminating the need for lengthy integrations.
With Imperum, connecting your technology is simple. Our no-code AI wizard lets you integrate any technology in just a few clicks. Plus, our Chrome extension lets you generate connectors in minutes, cutting down the time it would typically take by weeks.
In today’s complex technology landscape, many systems lack REST API support, making seamless integration a challenge.
As part of our Hyperautomation capability, our AI-powered Utilities feature eliminates this hurdle by enabling effortless integration with various protocols—including Telnet, SSH, RDP, Webhooks, and CLI—without requiring any coding.
This solution enables you to connect with legacy systems and technologies that don’t support modern API standards, ensuring operational efficiency and compatibility across your entire tech ecosystem.
Our feature-rich Casebook serves as a comprehensive hub for all incident-related data, providing a complete overview of your security environment.
With the ability to generate unlimited cases -both manually and automatically- it acts as a dynamic library of past incidents.
This empowers retrospective analysis, helping you identify patterns and trends to improve future incident management and facilitate quicker resolutions.
Explore how Imperum’s AI-driven features enhance SecOps efficiency and security operations.
Select a module to explore how you can transform your security operations with intelligent automation.

With our borderless integration capability, connect effortlessly with your existing security infrastructure through a convenient Chrome plugin.
Ingest data into the Imperum SOC Platform without the need for native connectors, ensuring a seamless and efficient security operation.
SecOps with
Cloud-Based AI
Leverage the power of cloud-based Large Language Models (LLMs) to assist your SecOps team in alert analysis, threat hunting, and forensic response.
Our solution optimizes daily operations, providing intelligent insights and automation for faster, more effective real-time decision-making.
Our AI-Powered Auto Case Assignment feature enhances the productivity of your security teams by intelligently assigning cases to the most qualified analysts.
This advanced, air-gapped solution continuously learns from your team’s behaviors and incident patterns, ensuring each case is assigned to the right expert.
By leveraging analysts’ strengths and past performance, our system optimizes workflows and boosts response efficiency.
Rapid and Accurate Incident Management
Our revolutionary AI-Powered Auto Triage Agent transforms incident response by automatically assessing the severity and nature of security events in real time.
It intelligently prioritizes cases based on threat level and potential impact, ensuring the most critical incidents are addressed first.
By automating and enhancing the triage process, it accelerates decision-making, reduces response times, and minimizes organizational risk.
With this powerful feature, your SecOps team can concentrate on tackling the most pressing threats, maintaining operational security, and effectively reducing the overall threat landscape.
Your security journey doesn’t end here—it’s an ongoing process. Imperum seamlessly guides you through ingestion, detection, and hyperautomation, leading into response, forensics & investigations, and threat hunting. With robust AI-powered capabilities at every stage, Imperum ensures comprehensive protection throughout the entire security lifecycle.
Harness the Power of 600+ Predefined Artifact Collectors for Unmatched Digital Forensics & Incident Response
Our innovative Incident Response and Forensic tool combines EDR visibility with powerful forensic capabilities, simplifying complex data breaches for faster, more efficient investigations.
Key Benefits
- ✦
Comprehensive Visibility:
Empowers your EDR with in-depth forensic analysis
- ✦
Faster Response:
Streamlines breach management for quick resolution
- ✦
Unmatched Insight:
Access to the most extensive library of predefined, community-powered artifact collectors
- ✦
Precision & Ease:
Empowers your team to address even the most intricate breaches with confidence
This cutting-edge solution enables rapid, accurate threat resolution, putting you in full control while offering a new level of control in managing and mitigating breaches.
Compatibility with
Community Supported Artifacts
Built-in
Host-Isolate Function
Agentless Collection
Microscopic Forensics Capability
Full Remote Bash & PowerShell Access
Tailored Threat Hunting for Maximum Impact
To further enhance your investigative capabilities, our platform offers flexible threat-hunting options to suit your operational needs. Whether you require a one-time, large-scale hunt to uncover hidden threats or a continuous, proactive approach to track persistent adversaries, you have full control over your security strategy.
Select the modules to gain deep visibility into forensic artifacts, live system telemetry, process execution, network activity, and more—empowering you to act with precision and confidence
Our On-Demand Threat Hunting function actively hunts threats in Forensics whenever needed. By conducting detailed behavior analysis, it uncovers threats that often bypass traditional alarms.
Users can initiate targeted threat sweeps on-demand, offering a flexible, responsive approach to threat detection and ensuring you stay ahead of potential risks.
The Continuous APT Hunter is designed to actively detect and mitigate Advanced Persistent Threats (APTs) that often evade traditional detection methods. By focusing on behavioral analysis, this powerful tool identifies threats that do not trigger conventional alarms, uncovering the subtle patterns and behaviors associated with APTs.
With the Continuous APT Hunter, you can set up periodic threat hunts targeting specific servers or endpoints, scanning for key APT behaviors such as:
Stop Threats Before They Escalate
Our Advanced Threat Detection capability seamlessly integrates endpoint detection with digital forensics, leveraging SIGMA rules to identify and neutralize threats in real-time.
Our AI-driven automation enables instant forensic analysis through dynamic playbooks, eliminating manual complexity and accelerating incident response.
This isn’t just detection - It’s proactive, intelligent defense designed to stop threats before they escalate.
Automated Investigation and Response (AIR)
Communicate Directly with Processes,Not Just REST-APIs
Our groundbreaking solution enables direct interaction with processes, bypassing the limitations of traditional REST-API connections. Powered by the combined strength of Forensics and Automation, this award-winning capability is seamlessly integrated into your playbooks, empowering your security teams like never before.
With Forensics and Automation, you can fully automate Digital Forensics and Incident Response (DFIR) tasks through customizable playbooks. This unique functionality allows responders to design specialized workflows tailored to specific forensic needs, streamlining complex investigations and incident response processes.
Not Convinced Yet? Security at Your Fingertips – Anytime, Anywhere
We know how crucial it is to stay in control of your security and respond to threats in real-time. That’s why we developed our mobile app—putting all your alerts and open cases directly on your phone, so you can take immediate action wherever you are.
Seamlessly integrated with your security environment, it empowers you to respond quickly and effectively, ensuring your organization remains protected 24/7.
